Summary
- Introduction
- Content Overview
- My Experience
- Quick Tricks & Tools
- Conclusion
1. Introduction
The HTB Dante Pro Lab is a challenging yet rewarding experience for anyone looking to level up their pentesting skills. It immerses you in a realistic enterprise network, teaching essential techniques like lateral movement and privilege escalation. Having completed it successfully, I’m excited to share my honest review along with a few quick tricks to help you navigate Dante more effectively!
In this lab, you’ll get hands-on practice with a variety of critical skills, including:
- Enumeration
- Exploit Development
- Lateral Movement
- Privilege Escalation
- Web Application Attacks
This lab is perfect for anyone ready to tackle a highly realistic, enterprise-level penetration testing environment. It features 14 machines (including 13 exploitable machines and 1 firewall that is out of scope) and 27 flags to collect.
2. Content Overview
By completing the HTB Dante Pro Lab, I found that the difficulty level varies between easy and intermediate, depending on the specific machine you’re trying to exploit or escalate privileges on. While the HTB platform provides a general description of the lab, I discovered that it offers much more in terms of skill development.
One key skill you’ll sharpen in this lab is tunneling, which plays a crucial role in navigating the environment. Tunneling between hosts is not overly complicated once you understand the theory behind it. With practice, it becomes a straightforward process. The lab provides an excellent opportunity to master tunneling, as it is the key to progressing from one target to the next.
Below, I’ll provide a practical example of tunneling to help you better understand its importance. Additionally, in the Tricks and Tools section, I’ll share the tools I used during the lab and link to some helpful YouTube videos. These resources make it easier to learn and practice tunneling effectively.
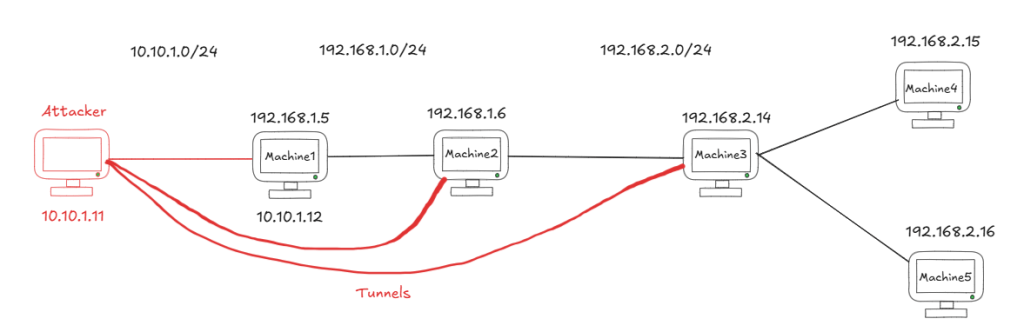
As shown in the figure, we have three different subnets. The attacker machine and the first target (Machine1) are in the same subnet. After compromising Machine1, we need to move to the next machine (Machine2). However, we can’t access Machine2 directly from the attacker machine because they are on different subnets. To overcome this, we can either use Machine1 to pivot into Machine2 or create a tunnel (best practice) that allows us to move, enumerate, and exploit Machine2.
The red paths in the figure represent the tunnels used for this purpose. Using the same concept, we can compromise Machine2 and then use it to gain access to Machine3, Machine4, and Machine5.
This simple figure is designed to make the concept of tunneling easy to understand for everyone.
3. My Experience
The Dante Pro Lab can be completed within a few days if you’re fully dedicated. For me, it took 12 days, as I worked on it for a few hours each night. The time required will vary for everyone. I did encounter some instances where machines went down, causing progress to stall until the specific machine was reset. However, overall, the experience was worth it, and I highly recommend this lab for anyone looking to enhance their pentesting skills.
I also recommend taking detailed notes of everything you find during the lab. Some machines require credentials or information that you will discover on other machines, so keeping organized notes is crucial. Make sure to thoroughly enumerate every exploited machine and gather as much information as possible, this will save you time and help you progress smoothly.
4. Quick Tricks & Tools
In this section, I’ll share some useful tools and tricks that were invaluable during the Dante Pro Lab:
- LinPeas: A fantastic script for discovering privilege escalation vectors on Linux machines. It automates the enumeration process, saving you a lot of time.
- WinPeas: The Windows counterpart to LinPeas, designed for uncovering privilege escalation opportunities on Windows systems.
- NetExec / CrackMapExec: These tools are incredibly helpful for enumerating and executing commands across multiple machines in a network. Use either one based on your preference, as both are great for lateral movement and credential spraying.
- Ligolo-ng: A powerful tool for tunneling and pivoting between machines. It allows you to create secure tunnels to access other subnets. I highly recommend checking out this video for a simple and effective tutorial on how to use Ligolo-ng for pivoting.
- Chisel: Another excellent tunneling tool that works well with ProxyChains. While I personally found Ligolo-ng easier to use, Chisel is still a solid choice for tunneling. For a tutorial on using Chisel effectively, refer to this video.
- BloodHound: You will need this tool when you encounter Windows machines that are part of an Active Directory (AD). BloodHound helps you visualize the AD environment and identify attack paths, making it easier to exploit any AD-related vulnerabilities.
- Metasploit: Metasploit is a must-have tool for exploiting vulnerabilities and automating tasks like reverse shell generation, privilege escalation, and post-exploitation. You can use its extensive exploit database and modules to target machines with ease.
Tips:
- Take Notes: Always take detailed notes about every credential, hash, and configuration you find. Some machines in the lab rely on information or credentials obtained from others.
- Thorough Enumeration: Spend enough time enumerating every exploited machine. Tools like
enum4linux,smbclient, and built-in commands likesysteminfooripconfigcan reveal critical information. - Use Port Scanning Tools: If
nmapisn’t available, use basicbashorPowerShellscripts to scan open ports (ncor loop-based ping scripts). - Be Patient: Some machines may require resets or additional digging to exploit successfully. Stay focused and experiment with different tools and methods.
5. Conclusion
The HTB Dante Pro Lab is an exceptional way to challenge and enhance your penetration testing skills. From real-world enterprise networks to advanced techniques like privilege escalation, tunneling, and lateral movement, this lab offers a comprehensive experience that pushes your limits. While the difficulty can vary, the sense of accomplishment after completing it is truly rewarding.
Take your time, document everything, and use the right tools to overcome obstacles. This lab is perfect for anyone eager to elevate their pentesting game and tackle complex, real-world scenarios. Enjoy the process, and remember the learning never stops!
